News broke yesterday that
Vic Gundotra is leaving Google. Many have supposed that Google+ is
dead in the water,
and its overt failure is something Google can’t come back from. I think
Google should look at this as a fresh start — and take the opportunity
to implement private sharing in a way that users love.
When Google initially launched Plus, it was clear they just wanted
users to move their sharing over from Facebook. Google+ didn’t give
users a new way to interact, it just copied another social network’s
model. As a result, Google’s social network attempt never truly took
off. Few people actively share on it. No one checks it. Most, in
general, ignore it.
This failure has been blamed on Google’s reputation for an inability
to build social products (a reputation Apple shares as well). But
looking deeper, I believe Google not only
can build social
products, but has a better shot than Facebook at building what the next
generation of social networking users want.
People want private sharing
Sharing on the Internet is moving to be more contextual and private. The single biggest insight in all our work and research on
Cluster
this past year is that more and more, people don’t want to share
everything with everyone, but instead share select content with select
people. They no longer just want to broadcast, and in turn, are
seeking an alternative to Facebook.
Startups are popping up left and right
to experiment in this space. Recently, ephemeral messaging and
anonymous sharing have been the loudest signs on this trend, but that’s
because they’re the easiest solutions. If the problem is you don’t want
photos to be accessible to everyone forever on Facebook, an easy
solution is for them to disappear seconds after being shared. If users
don’t want to be tied to things they posted years prior, or don’t want
certain people seeing what they’re sharing, making the posts completely
anonymous quickly solves it.
As Fred Wilson of Union Square Ventures recently
said,
“It’s more about the control than the ephemerality. With Snapchat, I
know who’s going to see this and I know it’s not going to move out
beyond that place.”
But that doesn’t mean those are the right long-term solutions. When
we’ve asked users about why they use these services, it’s largely
because they are no better alternatives for contextual sharing. Between
Facebook and Snapchat (or SMS or email), Facebook is not an option if
they’re worried about privacy.
Facebook knows this
Facebook is an incredible organization with more data about patterns
of human activity than any company on the planet. They see this coming
and are clearly trying to figure out how the growing customer desire for
contextual sharing will work within Facebook. “The [next big trend]
that we’re seeing now is sharing with smaller groups,”
says Mark Zuckerberg.
There are lot of small things Facebook is doing to prepare for this battle.
- The latest Facebook iOS app includes a subtle microsharing feature.
- They’ve hinted at a future Facebook Groups app.
- They recently decided to remove messaging from the core Facebook app ( forcing users to instead use the dedicated Messaging app).
These are strategic initiatives to decouple a user’s public Facebook
experience with these more private interactions. They’re starting to
train users to not think of Facebook as one public place, but a set of
contextual experiences.
Facebook’s biggest problem: public perception
Facebook isn’t recognized as a place to be private. It’s cemented in
the average user’s mind as a place to share publicly. TechCrunch writer
Josh Constine
recently touched on this:
The public perception of Facebook was firmly rooted in
the idea of sharing things your boss or family might see, and that
everything posted was tattooed on your profile.
And given the rocky history with changing privacy policies, users
don’t tend to trust Facebook even if what they’re sharing is marked as
private. Constine writes:
We just might not be able to escape the lurking fear that
even if Facebook offered an anonymous sharing option, posts would
somehow come back to haunt us.
To get a better sense of real user perception of Facebook, we asked 16
user testing participants about their Facebook usage. Twelve responded with concerns over privacy and sharing visibility:
- “I use Facebook when I want to share to a more general group of
people and kind of put down those memories as a part of my timeline.”
(Seattle)
- “I don’t really post pics on Facebook because I’m nervous about who else would be seeing them.” (34, homemaker, San Francisco)
- “Unless you don’t have the settings set up right on Facebook, then
it’s all over the place.” (26, territory sales rep, Nashville)
- “I’m always changing my settings on Facebook when I post a picture,
like, ‘who can see this or not?’—I’m always getting grief from family,
like, ‘why did you post that!?” (44, construction manager, San
Francisco)
- “A small group of friends you want to share specific photos with—not
necessarily blasted on Facebook with, like, 400 people.” (37, teacher,
San Francisco)
- “[Private sharing] is possible to do on Facebook, but it’s harder
for people to do and more confusing. It’s pretty much like you have to
share with everyone or no one” (25, hospital assistant, San Francisco)
- “My friends don’t care about certain pictures that my family would
care about and vice versa.” (24, social media strategist, Nashville)
- “Seems like the big thing with Facebook: the whole privacy thing is
blowing up. Everyone sees so much, whether you want ‘em to or not.” (42,
musician, Nashville)
- “Sometimes you don’t want certain people to look at your photos, like, ‘hmm should I post this?” (19, student, San Francisco)
- “We would share funny content, like, it could be a picture you took
of one of my fraternity brothers dancing at the party or whatever just
doing stupid stuff that you know you can’t put on Facebook.” (22,
intern, Nashville)
- “On Facebook everybody can see what you’re posting.” (42, self-employed, San Francisco)
- “Facebook, I thought, was at its peak when it was only for college students.” (26, culinary student, San Francisco)
There is little doubt Facebook has enormous work to do to earn the trust of its users as a place to post privately.
Google’s biggest strength: public perception
Although not seen as the most innovative company in the world when it
comes to social products, Google has consistently maintained consumer
confidence for handling sensitive user information across a wide range
of products.
Email might be the most private sharing of all, yet hundreds of
millions of people communicate daily through Gmail. Google Docs are used
by countless individuals and businesses to share and store private
documents and make small team collaboration easier. GoogleTalk is a
massively used private messaging service.
Google Hangouts is a small
group collaborative conferencing service. Google even has a product
called Groups, which is a mostly forgotten version of the web forums of
web 1.0.
The point is, not only do people trust Google to keep their private
information private, but Google has a bunch of products where users are
already doing this.
Google’s good idea that never took off
Even though Google+ wasn’t that impressive, there were a few nuggets
of wisdom within. I’ve already mentioned Hangouts, which launched with
Google+, but the other is a feature most people have heard of, but no
one uses: Google+ Circles.
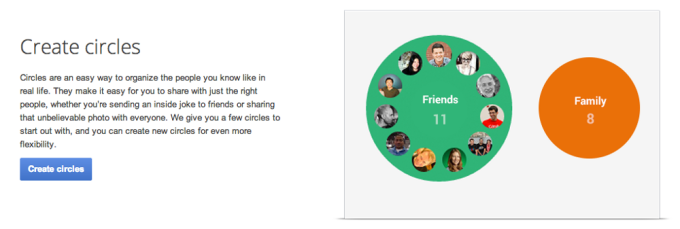
Surprisingly, during
our recent user testing,
people from all walks of life and geographies referenced Google+
Circles. Typically, they appreciate the concept but don’t use the
product. Two examples:
- “The concept of a group space makes me think of the whole Google+
thing, with, like, adding to circles and whatnot—which is a good
concept, but nobody bought into it so it didn’t work.” (26, culinary
student, San Francisco)
- “The first thing I thought about [when thinking of small groups]
were the circles on Google, but I think Google+ is forced and kinda
silly.” (29, administrator, Nashville)
While the idea of Circles is solid, it got mixed up in the execution
of Google+. Users are expected to set up these groups without any real
reason why, except some potential future benefit. And all within an
uninspiring social network.
While the current iteration of Circles failed, the concept made
perfect sense to users and fits the current social networking trend.
What Google should do
Google has an arsenal of quality products trusted by users for
private, contextual sharing. The next step is to fit them together in a
way that makes sense to a user looking for a Facebook alternative. I
have absolutely no insight into what’s going on at Google, but I would
start with focusing on a new product simply called Google Groups
(renaming the existing “Groups” product to Google Forums).
Google Groups would be a standalone mobile and web experience where users could:
- send messages (powered by Google Talk)
- video chat (powered by Google Hangouts)
- share files (powered by Google Drive)
- post photos and videos (a mix of Google Photo Party and a simplified form of Google+)
The groups themselves would be an evolution of Google Circles. All
activity would be historically recorded and only accessible to the
people who are specifically in the group. It would be completely
private, accessible only by invitation.
At Cluster we think we’re working on an interesting approach to
private group sharing, but our Achilles heel is that we lack the massive
installed user bases of Facebook and Google. While Facebook might
initially appear to be better positioned because of its historical
success with social products, its public perception puts it in a
vulnerable position, which Google, if it’s smart, will take advantage
of.
It should be an interesting few years.
 It’s no secret that PHP doesn’t always get the credit it deserves.
While the language has developed quite a bit over the last few years —
in large part thanks to capable frameworks and package support with Composer – it
still gets a bad rap. Some of that is deserved, given that it
can encourage beginners to write bad code (though we can also blame all
of the outdated PHP tutorials
and code snippets on the web for this). At the same time, though, it’s a
pretty easy language to pick up and in the right hands, it’s just as capable as any other server-side language.
It’s no secret that PHP doesn’t always get the credit it deserves.
While the language has developed quite a bit over the last few years —
in large part thanks to capable frameworks and package support with Composer – it
still gets a bad rap. Some of that is deserved, given that it
can encourage beginners to write bad code (though we can also blame all
of the outdated PHP tutorials
and code snippets on the web for this). At the same time, though, it’s a
pretty easy language to pick up and in the right hands, it’s just as capable as any other server-side language.